Yang Qing had 360 for 6 years "security".
In 360, Antony Yang research directions to be safe. His Unicorn development team responsible for the protection of the 360 company-wide network security products "day tour". This product now from 360 for personal use into a 2C enterprise wireless hotspot security management platform.
Antony Yang seldom attended "General Assembly" these occasions, but the way he talk sensibly about security but people didn't feel any hackers often "dull". In fact, he is on this year's 315 evening network security engineer.
Wearing VR glasses controlled UAV is a kind of

Unicorn Team is primarily responsible for radio and hardware-related security research, so they have a lot of exposure to hackers and hacker. Why are hackers attacking smart device? in Antony Yang's view, hacked smart devices can bring more fulfillment. "Website, but the website crashed. But attacking cars, personal safety may be subject to some loss. 」
In the eyes of Antony Yang, perhaps this is a devastated world, because it is full of loopholes.
Hardware vulnerabilities: of all things Internet war
All things Internet times, each link may be loopholes, but each vulnerability can affect the entire ecosystem.

Internet architecture is still more traditional, ends, clouds are the hardware itself. Our mobile tablet is a Terminal, this is the most common type of equipment. Cloud is the traditional interface of server resources. Hardware now mainly refers to the intelligent hardware. Speaking of risk, there are three aspects of risk, risk, server side risks and risks of the hardware itself.
Antony Yang and his team are doing an experiment, they forged a smart home devices, cloud platform to deliver real environmental data, ultimately renders wrong data on the mobile terminal. Data should be provided by the sensors, but this aspect of the application of the vulnerabilities of cloud services, and eventually gets completely wrong as a result of environmental monitoring data. This is an example of a typical hardware application vulnerabilities is applied. "Sometimes you get a device that can handle all the company's products. 」
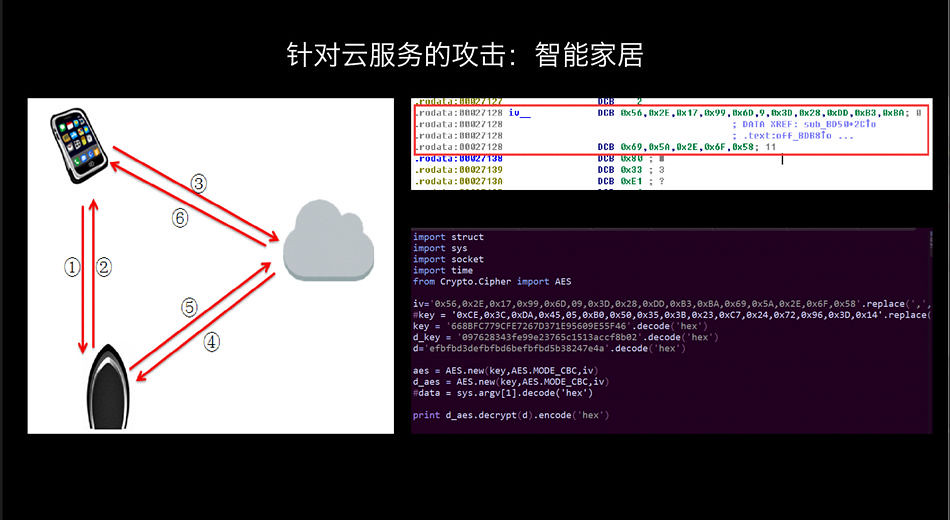
Of course, for the Center attack should not be ignored. Antony Yang smart outlets, for example, use the UDP transport is taboo on security applications. When this device uses AES encryption, will lead the attack succeeds a device equivalent to all equipment for a successful attack.
Hardware the physical layer vulnerabilities, Antony Yang referred to an example. As by bus, interface attack car ECU module. Hardware reverse analysis of the hacker used methods there are many, such as dismantling of contact, circuit, find the serial port, such as JTAG. Antony Yang also refers to the TTL of the router interface TTL interfaces and JTAG interface, electrical boxes, and so on.
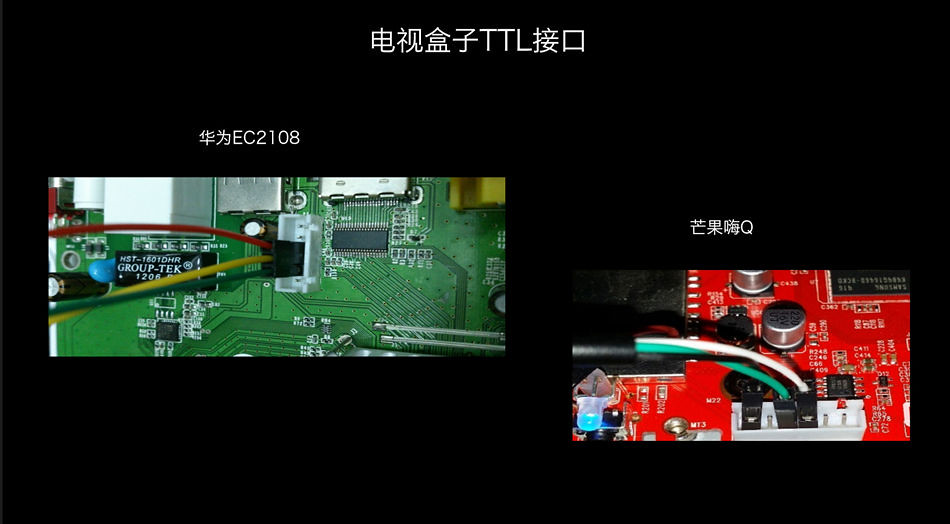
Many hardware physical vulnerability, we can what protection? Yang Shu feels the need to focus on 4 aspects: first of all is the location interface hidden as much as possible, and the second is to use a special plug-in and unconventional interface, and the third is to use special linear order and, finally, can design separate debug interfaces, use signal or encryption chips.
Wireless communications: a ubiquitous
Attacks on wireless communication, geek Park described previously in the hacker world, focus, passion, talent and ability is the hard currency of the article already has a very detailed description.
Antony Yang on the spot focus gives the example car wireless RF signal to attack. Safety conferences they do regular on-site examination of how to break a car door. Now, when many of the cars designed for cost reasons, will only consider whether the RF signal is an effective device, and does not detect and analyze whether the owner around the car, this gives Antony Yang some "opportunities".
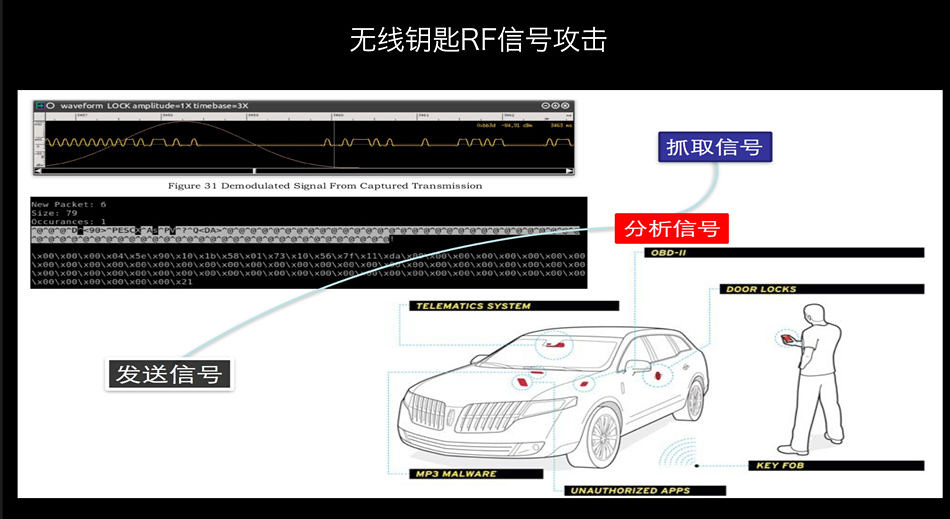
When in auto modulations, Yang Qing found whether Audi or the public, Chery is Volvo, debugging in a similar way. Among them, some more considerations than other manufacturers BMW and Volvo.
Antony Yang to run his own car and also has a special plug-type tire pressure sensor. Through two days of analysis, data restore, for some decoding. Finally, access to the specific data structures, understanding the data encryption methods. Specific encryption method is put in front of the digits are added together and then divided by two, and finally arrive at a result. This level of encryption for security researchers is very low. Antony Yang and his partner were experimentally sends entirely the wrong data to the tire pressure sensor, realizes the effect of random control automobile tyre pressure, tire pressure can be easily transferred back to normal.
Drone aircraft flying for the now very popular, Yang Qing's team also did not want to miss. Within the six-ring, drones are grounded, GPS chip detects no specific location, if in the no fly zone will lock the machine cannot take off. They cheat through GPS signals the end to drone on the rooftop of 360 companies flew up. In the eyes of Yang Qing, spoofing GPS modules just for fun, there is no special difficulty and fun. The really interesting things for this vulnerability can achieve new possibilities. "No fly zone for drone is a double-edged sword, unmanned aerial vehicle detected everywhere in the no fly zone, unmanned aerial vehicles will drop, the drop operation on the part of the drone is unconditionally enforceable. We give it a false position signal of Tiananmen Square, fell as soon as it detects is a restricted area. Under such circumstances, we can imagine some hijacked the drone. 」
3G, 4G by the network will use communication technology. Under current 2G, Yang Qing and his team can be hijacked. Antony Yang recommended that car makers future force binding 3G or 4G of the telematics network, because hackers can easily use their own equipment to build a 2G network. Then hackers will make your device is connected to its network, allow you to flow through its base stations, traffic hijacking.
No comments:
Post a Comment